
Provides comprehensive protection, ensuring integrity, confidentiality, and availability of your data and resources!
Bonelli File Protection is a secure and scalable file and folder backup service that enables MSPs to efficiently protect and recover data across client devices. Simple, SMB-friendly, endpoint file backup, with powerful MSP-centric capabilities that automate service delivery and minimize operational overhead.
With File Protection you never need to worry about your files again. With its MSP-centric capabilities and automated service delivery, protecting your files has never been easier.

Centralized Configuration and Remote Deployment
Automated authentication and customer data backup without impact on client productivity.
Continuous File and Folder Backup
Backup locations are continuously scanned for changes with backups functioning over any Internet connection. All files retain version history for up to 180 days.
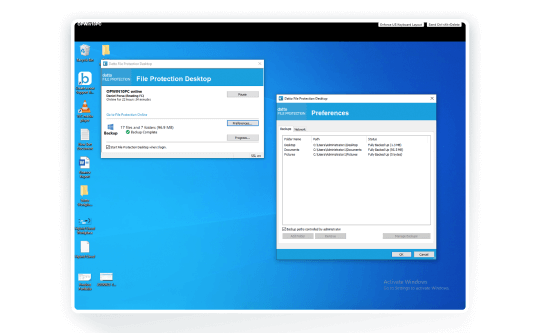
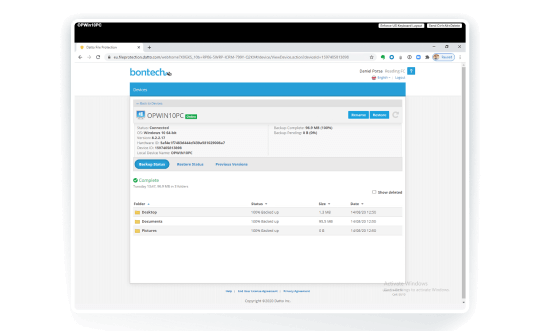
Self-Service Restore
Clients can access their own backup files, helping to drive down support requests.
With Bonelli Endpoint Detection and Response (EDR) you can detect and respond to advanced threats. EDR is an easy to use cloud based EDR solution that’s designed for your business.
As many as 77% of advanced threats bypass up-to-date antivirus products. EDR enables you to detect and respond to sophisticated attacks. With its built in continuous endpoint monitoring and behavioral analysis deliver comprehensive endpoint defense.
Click-to-respond
Take action against advanced threats right from your alert dashboard. Isolate hosts, terminate processes, delete files, and more without wasting precious seconds.
Detect fileless attacks with behavioral analysis
Bonelli EDR includes patented deep memory analysis to ensure you’re informed of even the most elusive threat actors.
MITRE ATT&CK mapping
Our alerts are mapped to the MITRE ATT&CK framework to provide context and helpful clarity to your team, reducing the security expertise required to effectively respond.
Smart Recommendations
Our seasoned SOC analysts have distilled their experience into building automated mitigation recommendations for today’s advanced threats.
Scalable remote response actions
Once a threat is detected, it’s essential to mitigate it quickly. Our click-to-respond feature supports your team in taking action against cyber-attacks as quickly as possible to reduce potential damage.
Integrated EDR and RMM
Bonelli EDR integrates with Bonelli RMM for efficient and seamless endpoint management.

Comprehensive Endpoint Security
Enable managed service providers to protect your Windows and MacOS endpoints. With built-in advanced breach detection, event log monitoring and intrusion detection you can respond rapidly to an attack.

Real Time Network Security
Gain new levels of network protection with Datto Managed SOC. With real time threat reputation and malicious connection alerts you can respond to network attacks quickly.

Cloud Security and Monitoring
Take your security detection and response best practices to the cloud. It enables you to monitor and respond to Microsoft 365 malicious activity. It can also provides you with an overall Secure Score.
No Hardware Required
Deployment couldn’t be any easier, due to it being entirely cloud based. With no required hardware you can deploy Managed SOC with ease and reduce overhead by not maintaining expensive hardware.
Automated patch management
Take a proactive response to protecting endpoints. With Bonelli RMM’s patch management feature, you can deploy the latest patches to secure systems and reduce threat risks.
Ransomware detection
Ransomware is one of the most common cyber threats that face businesses today. Bonelli RMM has built-in ransomware detection to help you monitor and respond to attacks.
Keep your data secure with our data encryption services. Companies should implement encryption to protect data endpoints should an attacker breach their security measures or gain access to their devices.
Data Security
The key reason for deploying endpoint encryption is to safeguard sensitive data against leakage and unauthorized access. With endpoint encryption, an attacker that has physical access to a device won’t be able to access the information it contains.
Regulatory Compliance
Deploying endpoint encryption on devices that contain sensitive data protected by data regulations can be crucial to attaining compliance with some regulations.
Malware Defense
Endpoint encryption can help make your devices less vulnerable to malware attacks.



